Crypto Guide: Cryptocurrency Wallets
Last Update: August 29th, 2024
A cryptocurrency wallet is a secure digital tool that allows individuals to store, manage, and interact with their crypto assets. Unlike a traditional wallet, it doesn’t hold actual coins but instead stores cryptographic keys—public and private—that provide access to the coins on the blockchain.

These wallets are essential to the blockchain ecosystem, enabling users to send, receive, and monitor their cryptocurrencies. Storing your assets on exchanges might seem convenient, but it exposes them to unnecessary risks. To safeguard your digital investments, it’s crucial to use a reliable cryptocurrency wallet tailored to your needs.
FX Leaders is committed to conveying accurate and unbiased information about the different service providers in the cryptocurrency industry. Like with crypto exchanges and cryptocurrency platforms, finding a quality cryptocurrency wallet is essential for ensuring safe and easy access to your crypto.
In this guide, we’ll explore the various types of wallets, including hot, cold, and hardware wallets, to help you choose the right one for your assets. Cold wallets, such as hardware and paper wallets, offer robust protection by keeping your assets offline and away from potential cyberattacks.
How Cryptocurrency Wallets Operate: The Role of Public and Private Keys
At the core of how crypto wallets work are two cryptographic keys: the public key and the private key. The public key is akin to an account number; it is shared with others to receive funds. On the other hand, the private key is more like a password, granting the owner access to their funds and the ability to sign transactions.
The private key must remain confidential, as anyone with access to it can control the associated cryptocurrency. When a transaction is initiated, the private key is used to generate a unique digital signature, which is then verified by the network using the corresponding public key.
Wallet Addresses: The Key to Crypto Transactions
Every cryptocurrency wallet generates a wallet address, which is a compressed and shortened version of the public key. This wallet address serves as the destination for any funds sent to the wallet.
When a user wishes to receive cryptocurrency, they provide their wallet address to the sender, who then inputs this address in the transaction.
The transaction is then broadcasted to the network, where it is confirmed and added to the blockchain.
Types of Cryptocurrency Wallets

Cryptocurrency wallets are available in the following types of crypto wallets:
- Hot Wallets vs. Cold Wallets
- Software Wallets
- Desktop Wallets
- Mobile Wallets
- Web-Based Wallets
- Hardware Wallets
- Paper Wallets
- Custodial vs. Non-Custodial Wallets
Here are our top recommendations for the best crypto wallets currently available:

- Exchange different assets on the device.
- Supported by different crypto clients.
- Compatible with different operating systems.
- Full control over private keys.
Cold storage

- Shapeshift is built into Exodus.
- Easy-to-use interface.
- Ideal for beginners.
- Beginner friendly
- Numerous cryptos available.
- Encrypted private keys controlled by clients.
Augur
Funfair
Bitcoin & Bitcoin cash (BCH)
Dash
Ether (Ethereum)
Ethereum Classic (ETC)
Litecoin (LTC)
Hot storage

- Full control over private keys.
- Two-factor authentication.
- Increased private key security.
- Supports a variety of cryptos.
Litecoin
Dash
Ether (Ethereum)
Ethereum Classic (ETC)
Zcash
Dogecoin
Namecoin
Cold storage


- Compatible with numerous cryptocurrencies.
- Greatly increased security, even when PC security is compromised.
- Full control over private keys.
- Choose between Ledger Blue and Ledger Nano S.
Cold storage

- Hierarchical Deterministic wallet.
- Full control over private keys.
- Excellent user interface.
- Shapeshift enables exchange between numerous cryptos.
Ether (Ethereum)
Dash
Zcash (ZEC)
Ethereum Classic (ETC)
Hot storage
More About Cryptocurrency Wallets
Hot Wallets vs. Cold Wallets
At the most fundamental level, cryptocurrency wallets are categorized into hot wallets and cold wallets, with hot wallets being connected to the internet and offering convenience for easy access to cryptocurrencies. Each type offers distinct features and security paradigms.
Understanding the dichotomy between these two types is crucial for aligning your wallet choice with your security needs and transaction habits
Defining Hot Wallets
Hot wallets are cryptocurrency wallets that remain connected to the internet, facilitating quick and convenient access to digital assets. Due to their accessibility and ease of use, these wallets are predominantly used for everyday transactions.
Hot wallets come in various forms, including desktop applications, mobile apps, and web-based platforms.
Characteristics of Hot Wallets:
- Instant Accessibility: Users can readily access their funds from anywhere with an internet connection.
- User-Friendly Interfaces: Designed with intuitive interfaces suitable for both novices and experienced users.
- Versatility: Support for multiple cryptocurrencies and integration with various services and platforms.
- Real-Time Transactions: Enable swift execution of transactions, making them ideal for active traders and frequent transactors.
Defining Cold Wallets
Cold wallets, in contrast, are offline storage solutions designed to provide enhanced security for cryptocurrency holdings. By keeping the private keys disconnected from the internet, cold wallets significantly reduce the risk of unauthorized access and cyber-attacks. These wallets can come in various forms like USB sticks or even paper, highlighting their advantages in security over hot wallets.
Cold wallets are typically embodied in hardware devices or physical mediums like paper.
Characteristics of Cold Wallets:
- Enhanced Security: Isolation from the internet mitigates exposure to hacking and malware threats.
- Long-Term Storage: Ideal for storing large amounts of cryptocurrency over extended periods.
- Physical Control: Ownership is maintained through physical possession of the wallet device or medium.
- Reduced Convenience: Accessing funds requires physical interaction with the wallet, making it less suitable for frequent transactions.
Key Differences Between Hot and Cold Wallets
| Aspect | Hot Wallets | Cold Wallets |
| Connectivity | Constantly connected to the internet | Remain offline; connect only when necessary |
| Security Level | More susceptible to online threats like hacking and phishing attacks | Offers superior security against online threats due to offline storage |
| Accessibility | Highly accessible; suitable for quick and frequent transactions | Less accessible; designed for secure, long-term storage |
| Convenience | Extremely convenient with user-friendly interfaces | Less convenient; requires physical access and additional steps to conduct transactions |
| Usage Scenario | Ideal for daily trading and regular transactions | Best suited for holding large amounts of cryptocurrency over long durations |
Pros and Cons of Hot Wallets
Pros:
- Immediate Access: Funds can be accessed and transferred instantly, facilitating timely transactions.
- Ease of Use: Simplified interfaces and processes make them suitable for users of all experience levels.
- Multi-Platform Support: Availability across various devices including computers, smartphones, and tablets.
- Integration Capabilities: Seamless integration with exchanges, payment services, and decentralized applications.
Cons:
- Security Risks: Persistent internet connection exposes them to potential cyber threats such as hacking and malware.
- Vulnerability to Phishing: Users may fall victim to deceptive schemes aiming to steal private keys or login credentials.
- Dependence on Third Parties: Some hot wallets rely on external services, which may pose additional security and trust concerns.
- Limited Control: In certain cases, users may not have full control over their private keys, increasing reliance on the service provider.
Pros and Cons of Cold Wallets
Pros:
- Superior Security: Offline storage significantly reduces exposure to online attacks and unauthorized access.
- Control Over Private Keys: Users maintain complete control and ownership of their private keys.
- Durability: Physical devices and mediums can be securely stored and protected against digital threats.
- Ideal for Large Holdings: Provides peace of mind for investors holding substantial amounts of cryptocurrency.
Cons:
- Reduced Accessibility: Accessing and transferring funds can be cumbersome and time-consuming.
- Physical Risks: Susceptible to loss, theft, or damage if not stored properly.
- Initial Cost: Hardware wallets entail upfront costs, which may be a barrier for some users.
- Technical Complexity: Setting up and using cold wallets may require a higher level of technical understanding.
Software Wallets
Software wallets represent a versatile and widely-used category of hot wallets, offering a blend of convenience and functionality tailored to diverse user needs. When setting up a crypto wallet, it is crucial to choose the right type and implement the necessary security measures to safeguard cryptocurrency assets. These wallets exist in various formats, including desktop applications, mobile apps, and web-based platforms, each catering to specific use cases and preferences.
Desktop Wallets
Desktop wallets are software applications installed directly onto a user’s computer, providing a secure and accessible means of managing cryptocurrencies. They offer a balance between security and convenience, making them a popular choice among both casual users and seasoned investors.
Features of Desktop Wallets:
- Enhanced Security Measures: Since the private keys are stored locally on the user’s computer, security largely depends on the user’s practices and system protection measures.
- Wide Cryptocurrency Support: Many desktop wallets support multiple cryptocurrencies, enabling users to manage diverse portfolios from a single interface.
- Advanced Functionalities: Some desktop wallets offer additional features such as integration with hardware wallets, support for decentralized exchanges, and customizable transaction fees.
- Offline Capabilities: Certain desktop wallets allow for offline transaction signing, adding an extra layer of security by minimizing online exposure.
Popular Desktop Wallets:
- Exodus: Known for its intuitive interface and extensive cryptocurrency support.
- Electrum: A lightweight Bitcoin wallet renowned for its speed and security features.
- Atomic Wallet: Offers support for numerous cryptocurrencies and includes built-in exchange services.
Advantages:
- Control Over Private Keys: Users retain full ownership and control of their private keys.
- Robust Security: When combined with proper security practices, desktop wallets provide a secure environment for managing funds.
- Feature-Rich Interfaces: Access to detailed transaction histories, portfolio tracking, and other advanced functionalities.
Disadvantages:
- System Vulnerabilities: Susceptible to malware and viruses if the host computer is compromised.
- Limited Mobility: Access is restricted to the specific device where the wallet is installed.
- Technical Requirements: Installation and maintenance may require a basic understanding of software management.
Mobile Wallets
Mobile wallets are applications designed specifically for smartphones and tablets, offering unparalleled convenience and portability. They are particularly suited for users who require on-the-go access to their cryptocurrency holdings and wish to conduct transactions seamlessly from their mobile devices.

Features of Mobile Wallets:
- Quick Transactions: Facilitate instant sending and receiving of cryptocurrencies, making them ideal for everyday purchases and peer-to-peer transfers.
- User-Friendly Design: Optimized interfaces for mobile devices ensure ease of navigation and operation.
- Additional Functionalities: Many mobile wallets incorporate features like QR code scanning for swift transactions, biometric authentication for enhanced security, and integration with mobile payment systems.
- Notifications and Alerts: Real-time updates on transaction statuses and market movements keep users informed and responsive.
Popular Mobile Wallets:
- Trust Wallet: Supports a wide array of cryptocurrencies and tokens, with a strong emphasis on security and privacy.
- Mycelium: A veteran Bitcoin wallet offering advanced features for both casual and professional users.
- Coinomi: Provides multi-currency support and a built-in exchange platform for convenient trading.
Advantages:
- Portability: Access your funds anytime and anywhere, provided there is an internet connection.
- Ease of Use: Simplified processes make it accessible even for cryptocurrency beginners.
- Additional Security Layers: Features like fingerprint recognition and facial ID add extra protection against unauthorized access.
- Versatility: Suitable for a variety of transactions ranging from small purchases to larger transfers.
Disadvantages:
- Security Risks: Loss or theft of the mobile device can pose significant security threats if proper precautions are not taken.
- Dependence on Device Security: Vulnerable to malware and phishing attacks targeting mobile platforms.
- Limited Storage: May not be ideal for storing large amounts of cryptocurrency due to inherent security concerns.
Web-Based Wallets
Web-based wallets, also known as online wallets, are accessed through web browsers and are hosted on cloud servers. They offer unmatched accessibility, allowing users to manage their digital assets from any device with internet connectivity and a browser.
Features of Web-Based Wallets:
- Universal Access: Accessible from various devices including desktops, laptops, tablets, and smartphones without the need for specific software installations.
- Seamless User Experience: Designed for ease of use with straightforward interfaces suitable for quick transactions.
- Integrated Services: Often linked with cryptocurrency exchanges, enabling users to trade and manage assets within the same platform.
- Automatic Updates: Benefit from continuous updates and maintenance handled by the service provider, ensuring up-to-date features and security protocols.
Popular Web-Based Wallets:
- MetaMask: A widely-used Ethereum wallet that facilitates interaction with decentralized applications.
- Blockchain.com Wallet: Offers support for multiple cryptocurrencies and provides additional services like trading and earning interest.
- Coinbase Wallet: Integrates seamlessly with the Coinbase exchange, providing an easy entry point for newcomers to the cryptocurrency space.

Advantages:
- Convenience: No installation required; simply log in through a web browser to access funds.
- Device Flexibility: Manage your assets from multiple devices and locations effortlessly.
- User-Friendly: Minimal setup and straightforward operation make it suitable for users with varying levels of technical expertise.
- Backup and Recovery Options: Providers often offer robust backup solutions to prevent loss of access due to forgotten passwords or other issues.
Disadvantages:
- Security Concerns: Storing private keys online increases vulnerability to hacking, phishing, and other cyber-attacks.
- Reliance on Third Parties: Users must trust the service provider to maintain security and integrity of the wallet.
- Potential Downtime: Service outages or maintenance periods can temporarily restrict access to funds.
- Privacy Issues: Some web wallets may require personal information, compromising user anonymity.
Security Features of Software Wallets
Ensuring the security of software wallets involves a combination of built-in features and user practices. Key security mechanisms include:
- Encryption: Protects sensitive data by encoding it, making it unreadable without the appropriate decryption key.
- Two-Factor Authentication (2FA): Adds an extra layer of security by requiring two forms of verification before granting access.
- Passphrase Protection: Utilizes complex passwords and seed phrases to secure wallet access and facilitate recovery.
- Regular Updates: Continuous software updates address vulnerabilities and enhance security protocols.
- Open-Source Code: Some wallets have publicly available code, allowing community scrutiny to identify and fix potential security flaws.
Conclusion on Software Wallets: Software wallets offer a versatile and convenient solution for managing cryptocurrencies, accommodating a wide range of user needs and preferences.
Hardware Wallets
In the realm of cryptocurrency storage solutions, hardware wallets stand out as one of the most secure and reliable options. These physical devices are engineered to provide robust protection for digital assets by keeping private keys isolated from online environments, thereby mitigating the risk of cyber threats.

Understanding Hardware Wallets
Hardware wallets are specialized electronic devices designed explicitly for storing cryptocurrency private keys offline. They function by securely generating and storing private keys within the device, ensuring that sensitive information never leaves the hardware. Transactions are signed within the device itself and then broadcasted to the blockchain via a connected computer or mobile device, maintaining a secure environment throughout the process.
Key Characteristics of Hardware Wallets:
- Offline Storage: Private keys are stored in a secure, offline environment, significantly reducing exposure to hacking and malware.
- Compatibility: Support for a wide range of cryptocurrencies, allowing users to manage multiple assets through a single device.
- User Authentication: Incorporates security measures such as PIN codes and passphrases to prevent unauthorized access.
- Tamper-Resistant Design: Built with robust materials and security features to detect and prevent physical tampering attempts.
- Portability: Compact and durable design facilitates easy transportation and storage.
Benefits of Using Hardware Wallets
1. Enhanced Security
The primary advantage of hardware wallets lies in their superior security features:
- Isolation from Online Threats: By keeping private keys offline, hardware wallets are impervious to most forms of cyber-attacks, including phishing, keyloggers, and remote hacking attempts.
- Secure Transaction Signing: Transactions are signed within the device itself, ensuring that private keys are never exposed to potentially compromised computers or networks.
- Advanced Encryption: Employs robust encryption standards to protect data stored within the device.
- Backup and Recovery Options: Provides secure methods for backing up private keys and recovering funds in case the device is lost or damaged.
2. User Control and Ownership
Hardware wallets grant users complete control over their digital assets:
- Self-Custody: Users retain full ownership of their private keys, eliminating reliance on third-party services.
- Transparency: Open-source firmware in some hardware wallets allows for community verification and auditing of security protocols.
- Independence from Platforms: Operates independently of exchanges and online platforms, reducing exposure to platform-specific vulnerabilities and failures.
3. Versatility and Compatibility
Modern hardware wallets offer extensive support and functionalities:
- Multi-Currency Support: Capable of storing and managing a diverse array of cryptocurrencies and tokens.
- Cross-Platform Compatibility: Works seamlessly with various operating systems and interfaces, including desktop and mobile applications.
- Integration with Software Wallets: Can be integrated with compatible software wallets for enhanced user experience and additional features.
- Regular Updates: Manufacturers provide firmware updates to introduce new features and address potential security concerns.
4. Ease of Use
Despite their advanced security features, hardware wallets are designed with user-friendliness in mind:
- Intuitive Interfaces: Equipped with screens and buttons that facilitate straightforward navigation and operation.
- Simple Setup Processes: Initial setup typically involves a guided process that helps users generate and secure their private keys efficiently.
- Convenient Transaction Processes: Conducting transactions involves a few simple steps, with confirmations required directly on the device for added security.
Popular Hardware Wallet Examples

1. Ledger Nano Series
The Ledger Nano series, including the Ledger Nano S and Ledger Nano X, are among the most acclaimed hardware wallets in the market.
- Features:
- Secure Element Chip: Utilizes a certified secure chip to safeguard private keys.
- Bluetooth Connectivity (Nano X): Enables wireless connection with mobile devices for increased convenience.
- Multi-Currency Support: Supports over 1,800 cryptocurrencies and tokens.
- Ledger Live App Integration: Offers a comprehensive application for managing assets, tracking portfolios, and conducting transactions.
- Robust Build Quality: Compact and durable design with a stainless steel cover for physical protection.
- Pros:
- High-level security with a proven track record.
- User-friendly interface suitable for both beginners and experienced users.
- Regular firmware updates and active community support.
- Cons:
- Ledger Nano S has limited storage capacity for applications compared to Nano X.
- Bluetooth functionality may raise security concerns for some users, although it is encrypted.
2. Trezor Model T
The Trezor Model T is a flagship hardware wallet known for its advanced security features and comprehensive cryptocurrency support.
- Features:
- Touchscreen Interface: Provides an intuitive and secure method for entering PINs and passphrases directly on the device.
- Open-Source Software: Allows for community auditing and transparency.
- Wide Cryptocurrency Support: Compatible with over 1,000 digital assets.
- Shamir Backup: Offers a secure and innovative method for backing up recovery seeds.
- U2F Authentication: Can be used as a universal second-factor authentication device for added online security.
- Pros:
- User-friendly with a responsive touchscreen.
- Strong emphasis on security and transparency.
- Versatile functionalities beyond cryptocurrency management.
- Cons:
- Higher price point compared to some competitors.
- Slightly bulkier design may affect portability.
3. KeepKey
KeepKey is a hardware wallet that combines security with an elegant design and straightforward user experience.
- Features:
- Large Display Screen: Facilitates easy transaction verification and management.
- Integration with ShapeShift: Allows for seamless cryptocurrency exchanges directly from the device.
- Robust Security Measures: Employs PIN protection and recovery sentence backup.
- Multi-Currency Support: Supports a variety of popular cryptocurrencies.
- Aluminum Casing: Provides durability and a premium look.
- Pros:
- Attractive and functional design with a focus on simplicity.
- Competitive pricing makes it accessible to a wide range of users.
- Smooth integration with exchange services enhances usability.
- Cons:
- Supports fewer cryptocurrencies compared to Ledger and Trezor devices.
- Larger physical size may be less convenient for some users.
Conclusion on Hardware Wallets: Hardware wallets offer an unparalleled level of security for cryptocurrency storage, making them an indispensable tool for serious investors and security-conscious users.
Paper Wallets
Paper wallets represent one of the most straightforward and cost-effective methods for storing cryptocurrencies offline. Despite their simplicity, they offer a high degree of security when created and managed correctly.

What is a Paper Wallet?
A paper wallet is a physical document that contains a printed copy of both the public and private keys required to access and manage cryptocurrency funds. These keys are often displayed as strings of alphanumeric characters and corresponding QR codes to facilitate easy scanning and transaction processing.
Key Characteristics of Paper Wallets:
- Offline Storage: Being a physical document, a paper wallet stores private keys offline, eliminating exposure to online threats such as hacking and malware.
- Cost-Effective: Requires no investment in hardware or software, making it an accessible option for all users.
- Simplicity: Easy to create and use without the need for advanced technical knowledge.
- Anonymity: Does not involve any digital footprint or association with online services, preserving user privacy.
Creating a Secure Paper Wallet
Creating a secure paper wallet involves meticulous steps to ensure that private keys are generated and stored without exposure to potential security risks. Follow this comprehensive guide to create a paper wallet safely:
Step 1: Prepare a Secure Environment
- Use a Clean Computer: Ensure that the computer used for generating the wallet is free from malware and viruses. Consider using a freshly installed operating system or a live boot from a trusted source.
- Disconnect from the Internet: For maximum security, disconnect your computer from all network connections before generating the wallet.
- Utilize Private Settings: Perform the process in a private and secure physical location to prevent any unwanted observation or interference.
Step 2: Choose a Reliable Paper Wallet Generator
- Select Trusted Services: Opt for reputable and open-source wallet generators such as BitAddress.org for Bitcoin or MyEtherWallet.com for Ethereum.
- Download Source Files: Instead of using the online version, download the generator’s source files from their official repository to use offline.
Step 3: Generate the Wallet
- Run the Generator Offline: Open the downloaded generator files in your browser while remaining disconnected from the internet.
- Follow Instructions: Follow the on-screen prompts to generate a new public and private key pair. Some generators may ask you to move your mouse randomly to create entropy and enhance security.
- Verify Information: Ensure that both keys are generated correctly and that the corresponding QR codes are clear and scannable.
Step 4: Print the Wallet
- Use a Secure Printer: Preferably use a printer that is directly connected to your computer via cable rather than a network printer to avoid potential interception.
- Print Multiple Copies: Create several copies to serve as backups, but be cautious about their storage.
- Use High-Quality Paper and Ink: To ensure longevity and legibility, print on durable paper with high-quality ink that resists fading and smudging.
Step 5: Securely Store the Wallet
- Choose Safe Storage Locations: Place the printed wallets in secure, dry, and discreet locations such as safes or safety deposit boxes.
- Protect from Physical Damage: Use protective sleeves or laminations to shield the paper from moisture, fire, and other physical threats.
- Avoid Digital Copies: Refrain from saving digital images or scans of the wallet to prevent digital exposure.
Additional Security Measures:
- Encrypt Private Keys: For added security, consider encrypting the private keys with a passphrase during generation, ensuring that only those with the passphrase can access the funds.
- Divide and Conquer: Store different copies in separate locations to mitigate the risk of total loss due to unforeseen circumstances.
- Destroy Digital Traces: After completing the process, delete any temporary files and clear your browser cache to eliminate residual data.
Using Paper Wallets Safely
Accessing and transacting funds from a paper wallet requires careful handling to maintain security:

Adding Funds to a Paper Wallet:
- Use the Public Address: To deposit cryptocurrencies, simply use the public address printed on the wallet as the recipient address in the transaction.
- Verify Transactions: Monitor the blockchain to confirm that the funds have been successfully transferred to the paper wallet address.
Spending or Transferring Funds:
- Import or Sweep Private Key: To access and spend the funds, you’ll need to import or ‘sweep’ the private key into a software wallet.
- Importing: Adds the private key to the software wallet, allowing access while keeping the funds linked to the original paper wallet address.
- Sweeping: Transfers the entire balance from the paper wallet to a new address in the software wallet, effectively emptying the paper wallet.
- Choose a Secure Software Wallet: Use a trusted and secure software wallet compatible with your cryptocurrency to perform the import or sweep.
- Conduct in Secure Environment: Perform the process in a secure and private setting, ensuring that your device is free from malware and connected through a secure network.
- Dispose of Used Paper Wallets Carefully: Once the funds have been transferred, destroy the physical paper wallet securely to prevent any potential misuse.
Advantages of Paper Wallets:
- Maximum Offline Security: Complete isolation from digital environments significantly reduces the risk of cyber-attacks.
- Cost-Effective Storage Solution: Requires minimal resources to create and maintain.
- Anonymity and Privacy: Does not involve personal information or third-party services.
- Simplicity: Straightforward creation and usage processes.
Disadvantages of Paper Wallets:
- Physical Vulnerability: Susceptible to damage, loss, or theft if not stored properly.
- No Partial Spending: Accessing funds often requires transferring the entire balance, which can be inconvenient.
- No Recovery Options: Loss or destruction of the paper wallet and backups results in permanent loss of access to funds.
- Technical Limitations: May be less suitable for users who require frequent access or transactions.
Conclusion on Paper Wallets: Paper wallets offer a secure and economical method for long-term storage of cryptocurrencies, especially for users who prioritize offline security and minimal interaction.
Custodial vs. Non-Custodial Wallets
Another critical distinction in the realm of cryptocurrency wallets lies between custodial and non-custodial solutions. This classification revolves around the control and ownership of private keys, significantly impacting security, responsibility, and user experience.
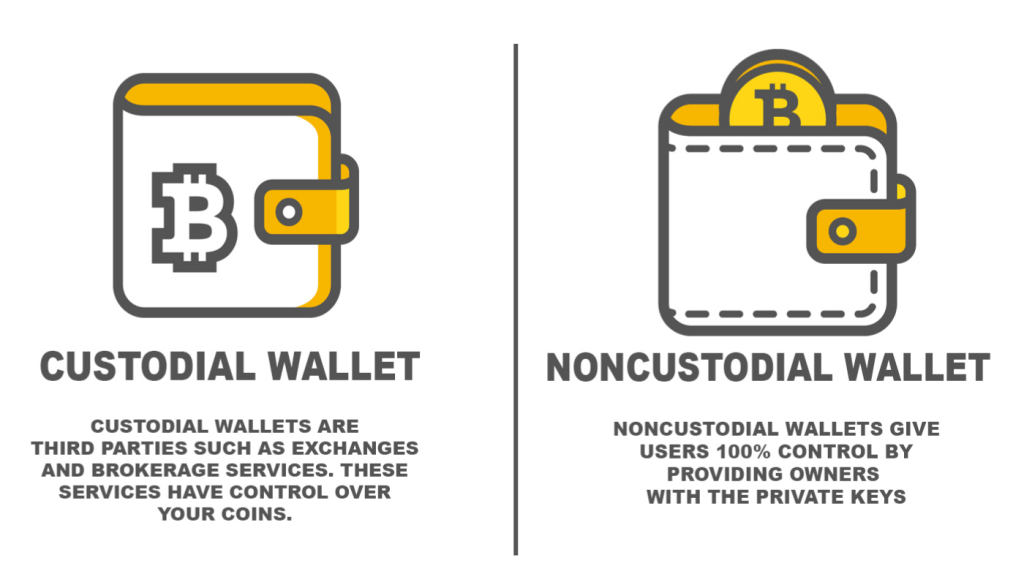
Understanding Custodial Wallets
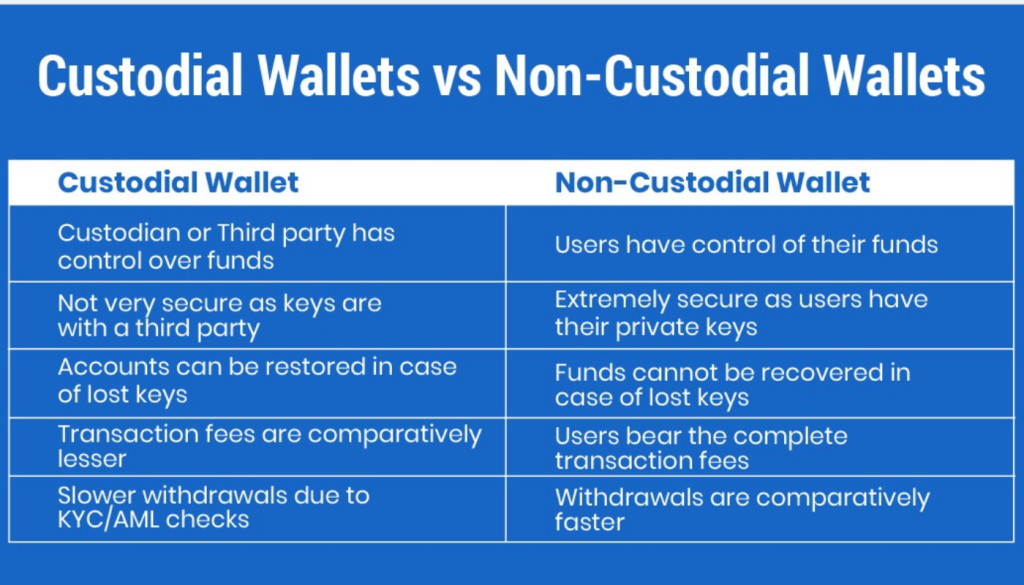
Custodial wallets are services where a third-party entity, such as a cryptocurrency exchange or financial institution, holds and manages the user’s private keys on their behalf. In this arrangement, users entrust the custody of their digital assets to the service provider, who is responsible for securing and maintaining access to the funds.
Key Characteristics of Custodial Wallets:
- Third-Party Control: The service provider holds and controls the private keys, effectively managing access to the user’s funds.
- User Convenience: Simplifies the management process by handling security and recovery mechanisms.
- Integrated Services: Often accompanied by additional features such as trading platforms, staking services, and customer support.
- Regulatory Compliance: Many custodial services adhere to regulatory standards, including Know Your Customer (KYC) and Anti-Money Laundering (AML) protocols.
Examples of Custodial Wallets:
- Exchange Wallets: Wallets provided by platforms like Coinbase, Binance, and Kraken, which allow users to store and trade cryptocurrencies.
- Online Wallet Services: Platforms such as Blockchain.com and Crypto.com offering wallet services alongside other financial products.
- Payment Services: Companies like PayPal and Robinhood offering cryptocurrency functionalities within their existing financial services.
Understanding Non-Custodial Wallets
Non-custodial wallets are solutions where users retain full control and ownership of their private keys, and consequently, their digital assets. These wallets do not involve third-party management, placing the responsibility for security and access entirely on the user.
Key Characteristics of Non-Custodial Wallets:
- User Control: Users are solely responsible for the generation, storage, and management of their private keys.
- Enhanced Privacy: Generally require minimal personal information, preserving user anonymity.
- Direct Blockchain Interaction: Transactions are processed directly on the blockchain without intermediary involvement.
- Greater Security Potential: Eliminates reliance on third parties, reducing exposure to centralized points of failure or breaches.
Examples of Non-Custodial Wallets:
- Hardware Wallets: Devices like Ledger, Trezor, and KeepKey where users manage their own keys.
- Software Wallets: Applications such as Exodus, Trust Wallet, and MetaMask that provide user-controlled storage solutions.
- Paper Wallets: Physical documents containing private and public keys managed entirely by the user.
Comparative Analysis of Custodial and Non-Custodial Wallets
| Aspect | Custodial Wallets | Non-Custodial Wallets |
| Control over Funds | Private keys are held and managed by a third-party service provider. | Users have full control and ownership of their private keys and funds. |
| Security | Security depends on the robustness and practices of the service provider; susceptible to centralized breaches. | Security depends on the user’s practices; eliminates centralized points of failure but requires diligent management. |
| Convenience | High convenience with simplified processes, password recovery options, and integrated services. | May require more technical knowledge and careful management; no recovery options if keys are lost. |
| Privacy and Anonymity | Often require personal information and adherence to regulatory protocols; less privacy. | Generally offer greater privacy and anonymity; minimal or no personal information required. |
| Transaction Speed | Transactions may be faster within the provider’s network but can be subject to delays during high network traffic. | Transactions are processed directly on the blockchain; speed varies based on network conditions. |
| Fees | May involve additional fees for services and transactions; fees set by the provider. | Transaction fees are directly related to blockchain network fees; users have control over fee settings. |
| Risk of Censorship | Subject to regulatory oversight and potential restrictions or account freezes. | Resistant to censorship; users can transact freely without intermediary interference. |
| Customer Support | Access to customer service and support for issues and queries. | Limited or no formal support; users rely on community resources and self-help. |
Pros and Cons of Custodial Wallets
Pros:
- Ease of Use: User-friendly interfaces and simplified processes make them accessible to beginners.
- Recovery Options: Ability to recover access through customer support in case of lost passwords or credentials.
- Integrated Services: Access to a wide range of services including trading, lending, and staking within the same platform.
- Customer Support: Availability of assistance for troubleshooting and queries enhances user confidence.
- Regulatory Compliance: Adherence to legal standards can provide a sense of legitimacy and trustworthiness.
Cons:
- Lack of Control: Users do not have direct control over their private keys, increasing dependence on the provider’s security measures.
- Security Risks: Centralized storage of keys makes them attractive targets for hackers; history of significant breaches in the industry.
- Potential for Account Freezes: Providers may restrict access to funds due to regulatory issues or internal policies.
- Privacy Concerns: Collection and storage of personal information can compromise user anonymity.
- Service Dependence: Users are reliant on the provider’s stability and continuity; service outages can affect access to funds.
Pros and Cons of Non-Custodial Wallets
Pros:
- Complete Ownership: Users have full control over their funds and private keys, aligning with the decentralized ethos of cryptocurrencies.
- Enhanced Security: Eliminates risks associated with centralized storage; security depends on user practices.
- Greater Privacy: Minimal personal information required, preserving user anonymity and privacy.
- Resistance to Censorship: Ability to transact freely without interference or restrictions from third parties.
- Flexibility: Users can choose and switch between different wallets and services seamlessly.
Cons:
- Responsibility for Security: Users bear full responsibility for securing private keys; loss of keys results in permanent loss of access.
- Technical Complexity: May involve more complex setup and management processes, posing challenges for less tech-savvy users.
- No Recovery Mechanism: Absence of customer support for recovering lost or compromised keys.
- Potential for User Error: Mistakes in handling or transacting can lead to irreversible losses.
- Transaction Fees: Users must manage and pay blockchain network fees directly, which can fluctuate and impact transaction costs.
Choosing Between Custodial and Non-Custodial Wallets
The decision between custodial and non-custodial wallets depends on individual preferences, risk tolerance, and intended usage:
Custodial Wallets Are Suitable For:
- Beginners: Users new to cryptocurrencies who prefer a guided and supportive environment.
- Active Traders: Individuals who frequently trade and benefit from integrated exchange services.
- Convenience Seekers: Users who prioritize ease of use and prefer not to manage private keys directly.
- Regulatory Compliance: Users who are comfortable with or require adherence to legal and regulatory standards.
Non-Custodial Wallets Are Suitable For:
- Security-Conscious Users: Individuals who prioritize maximum security and control over their digital assets.
- Privacy Advocates: Users who value anonymity and wish to minimize personal information disclosure.
- Long-Term Holders: Investors intending to hold cryptocurrencies over extended periods without frequent transactions.
- Decentralization Supporters: Individuals aligned with the principles of decentralization and self-sovereignty.
Conclusion on Custodial vs. Non-Custodial Wallets: By evaluating the pros and cons in relation to personal requirements and comfort levels, users can make informed decisions that align with their security needs and operational preferences.
Cryptos – A Booming Asset Class
With more and more institutions, retailers, and individuals using cryptocurrencies, the financial world is changing rapidly. Thousands of new participants are entering the crypto market every day for different reasons, which include international and local money transfers, investment and other speculative purposes, crypto mining activities, etc.
What is Bitcoin Currency?
Getting Involved in the Cryptocurrency Market
To get involved in the crypto market is really not complicated, especially with beginner-friendly wallets like KeepKey, Genesis, and Jaxx where individuals can also exchange different crypto coins for one another.
Crypto wallets are not the only means of engaging in crypto activities, however. Cryptocurrencies can be traded with CFDs on cryptocurrency trading platforms.
Then, of course, there are cryptocurrency exchanges where fiat and cryptos can be exchanged. Some of these exchanges offer margin trading in the same way that forex/crypto trading platforms do.

